Virus can make your Windows Vista to be Windows XP
Who says Windows Vista secure from viruses. At the time of launch may be a Windows Vista-claim in the safe from the virus. But time proved that man-made does not have the perfect and only a waiting time until only one OS in the successful exploration and found a way to mengeksploitasinya. This is evident from the virus Huhuhaha who are currently spread popularity in Indonesia mepumpuhkan the UAC (User Account Control) Windows vista is used to prevent unwanted programs run automatically without the user's computer.
Somehow related to what the global crisis that the world at this time (especially the computer world), the virus is a vbs virus with the theme "HUHUHAHA". Norman Security Suite detects virus variants "huhuhaha" page as vbs / Autorun.AO. (see image 1)

Picture 1, Norman Security Suite detect as VBS/Autorun.AO
Characteristics File Virus
Virus Huhuhaha be made using the VBScript programming language. Virus file size 6 kb, and can be spread so that it will automatically create a file that is facing "autorun.inf" which contains the script to run a virus file.
If the virus menginfeksi successful, it will create some files, the virus among:
· autorun.inf (all root drive)
· huhuhaha.vbs (all root drive)
· C:\WINDOWS\system32\XpWin.vbs
Virus will also copy the file "autorun.inf" and "huhuhaha.vbs" on each usb (flash / drive) that included on the infected computer. All files have virus RHSA file attributes (Read, Hidden, System, Archive), so it does not appear if the user does not display the hidden menu. (see picture 2)

Picture 2, Virus file huhuhaha or VBS/Autorun.AO
Symptoms of virus
· display the text on the virus “run”. (see picture 3)

Picture 3, Virus Text on pada Run’s menu
· Disable system restore. This is done so that the user can not restore the system settings back windows as before this virus infected.
· Adding the header text on the Internet Explorer . (see picture 4)

Picture 4, Header text on Internet Explorer
· Disable UAC (User Account Control) function on Windows Vista. UAC is a feature in Windows Vista that Microsoft claimed to make Vista more secure than Windows XP. The difference is a Windows pop up that impede the program (whether or not the virus program) is run automatically and the user's computer can still approve or deny the program to run. In many cases the virus attacks, users are upset with Vista UAC warning that repeated (because the virus is continuously trying menginfeksikan himself on the system) will tend to ignore the UAC warning and allow the program to run. In the case of the virus Huhuhaha this, the UAC has been considered by the virus so that the local need in order to disable memuluskan distribution. This again proves that in principle there is no OS is safe from virus attacks. The question is not "what the OS is safe from virus attacks? "But" Do you want to attack the virus OS or not? ". (see picture 5)
On Vista, this feature is used so that the user can run the program / command windows that need admin access rights. Next full article http://www.microsoft.com/windows/windows-vista/features/user-account-control.aspx

Picture 5, UAC (User Account Control) the attempt by disabled Huhuhaha
· Changing the name registered with the computer virus text. (see picture 6)
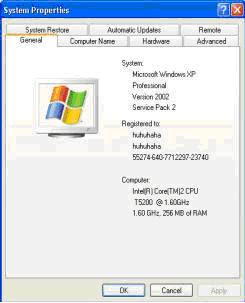
Picture 6, Information “Registered to: attempt by huhuhaha
· Disable “safe mode” function and make windows“blue screen” . When users try to log in through safe mode feature, the blue screen will appear. (see picture 7)

Picture 7, Blue Screen yang diakibatkan Huhuhaha jika user memasuki mode safe mode
· Blue Screen caused Huhuhaha mode if the user enters safe mode Automatic Updates, Firewall and Software Antivirus.
Distribution Method
The same as other local virus, the virus still huhuhaha using USB media (flash / drive) as a distribution. The virus will create the file "autorun.inf" and "huhuhaha.vbs" on each usb (flash / drive) that ditancapkan / dicolokkan on the infected computer. Both files will be automatically activated with only mengkases usb (drive / flash) is.
Modification Registry
To be able to run the current computer, the virus makes the following string :
· HKEY_LOCAL_MACHINE\SOFTWARE \Microsoft\Windows\CurrentVersion\Run
Ageia = C:\WINDOWS\system32\XpWin.vbs
· HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Systemdir = C:\WINDOWS\huhuhaha.vbs
To be able to appear on the menu Run, create a string of virus following :
· HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunMRU
a = huhuhaha
Even if it does not men-disable functions like the windows task manager, folder options, regedit, etc., disabled system restore to create a string with the following :
· HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\Windows NT\CurrentVersion\SystemRestore
DisableSR = 1
And disabled function UAC (User Account Control) to create the following string :
· HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\Windows\CurrentVersion\Policies\System
EnableLUA = 0x00000000
In addition, the virus add caption text on Internet Explorer with the following string to make :
· HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
Window Title = huhuhaha
Then, the virus also makes registration komputerdengan following string:
· HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\Windows NT\CurrentVersion
RegisteredOrganization = huhuhaha
RegisteredOwner = huhuhaha
So that text can appear at login windows virus, the virus makes the following string :
· HKEY_LOCAL_MACHINE\SOFTWARE\ Microsoft\Windows NT\CurrentVersion
LegalNoticeCaption = huhuhaha virus
LegalNoticeText = huhuhaha
To disable the function min-safe mode, "delete" the following string :
· HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot, AlternateShell
· HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\SafeBoot, AlternateShell
· HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Control\SafeBoot, AlternateShell
· HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot, AlternateShell
And deleted key following :
· HKEY_LOCAL_MACHINE\SYSTEM\ CurrentControlSet\Control\SafeBoot\Minimal
· HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network
Finally, try turning off the virus function with the Security Center to create the following string:
· HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center
AntivirusDisableNotify = 1
FirewallDisableNotify = 1
UpdatesDisableNotify = 1
Cleaning Virus
· Disconnect the computer that will be cleared from the network / internet.
· Turn off the virus is active in memory. Use the Windows Task Manager to kill the virus, with the name "wscript.exe". (wscript.exe is a windows file that is used to run a VBScript file). (see picture 8)

Picture 8, Turn off process with Windows Task Manager
· Delete the file following virus :
· autorun.inf (all root drive)
· huhuhaha.vbs (all root drive)
· C:\WINDOWS\system32\XpWin.vbs
Note
· We show the hidden files in order to facilitate the search process of the virus file. (file virus has the attributes Hidden, Archive, System, and Read-Only)
· To facilitate the search process should use the facility "Search" filter with the Windows autorun.inf file and *. vbs that have size 6 KB.
· Remove the registry string is created by the virus. To make the script can use the registry under this :
[Version]
Signature="$Chicago$"
Provider=Vaksincom Oyee
[UnhookRegKey]
HKLM, SOFTWARE\Microsoft\Security Center, AntiVirusDisableNotify, 0x00000000,0
HKLM, SOFTWARE\Microsoft\Security Center, FirewallDisableNotify, 0x00000000,0
HKLM, SOFTWARE\Microsoft\Security Center, UpdatesDisableNotify, 0x00000000,0
HKLM, SOFTWARE\Microsoft\Windows NT\CurrentVersion, RegisteredOrganization, 0, "Organization"
HKLM, SOFTWARE\Microsoft\Windows NT\CurrentVersion, RegisteredOwner, 0, "Owner"
HKLM, SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore, DisableSR, 0x00000000,0
HKLM, SYSTEM\ControlSet001\Control\SafeBoot, AlternateShell, 0, "cmd.exe"
HKLM, SYSTEM\ControlSet002\Control\SafeBoot, AlternateShell, 0, "cmd.exe"
HKLM, SYSTEM\ControlSet003\Control\SafeBoot, AlternateShell, 0, "cmd.exe"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot, AlternateShell, 0, "cmd.exe"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{36FC9E60-C465-11CF-8056-444553540000}, (default), "Universal Serial Bus controller"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E965-E325-11CE-BFC1-08002BE10318}, (default), "CD-ROM Drive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}, (default), "DiskDrive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E969-E325-11CE-BFC1-08002BE10318}, (default), "Standar floppy disk controller"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E96A-E325-11CE-BFC1-08002BE10318}, (default), "Hdc"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E96B-E325-11CE-BFC1-08002BE10318}, (default), "Keyboard"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E96F-E325-11CE-BFC1-08002BE10318}, (default), "Mouse"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E977-E325-11CE-BFC1-08002BE10318}, (default), "PCMCIA Adapters"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E97B-E325-11CE-BFC1-08002BE10318}, (default), "SCSIAdapters"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E97D-E325-11CE-BFC1-08002BE10318}, (default), "System"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{4D36E980-E325-11CE-BFC1-08002BE10318}, (default), "Floppy disk drive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{71A27CDD-812A-11D0-BEC7-08002BE2092F}, (default), "Volume"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\{745A17A0-74D3-11D0-B6FE-00A0C90F57DA}, (default), "Human Interfaces Devices"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\AppMgmt, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Base, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Boot Bus Extender, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Boot file system, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\CryptSvc, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\DcomLaunch, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dmadmin, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dmboot.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dmio.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dmload.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dmserver, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\EventLog, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\File system, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Filter, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\HelpSvc, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Netlogon, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\PCI Configuration, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\PlugPlay, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\PNP Filter, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Primary disk, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\RpcSs, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\SCSI Class, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\sermouse.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\sr.sys, (default), "FSFilter System Recovery"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\SRService, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\System Bus Extender, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\vga.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\vgasave.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\WinMgmt, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{36FC9E60-C465-11CF-8056-444553540000}, (default), "Universal Serial Bus controller"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E965-E325-11CE-BFC1-08002BE10318}, (default), "CD-ROM Drive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}, (default), "DiskDrive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E969-E325-11CE-BFC1-08002BE10318}, (default), "Standar floppy disk controller"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E96A-E325-11CE-BFC1-08002BE10318}, (default), "Hdc"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E96B-E325-11CE-BFC1-08002BE10318}, (default), "Keyboard"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E96F-E325-11CE-BFC1-08002BE10318}, (default), "Mouse"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}, (default), "Net"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E973-E325-11CE-BFC1-08002BE10318}, (default), "NetClient"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E974-E325-11CE-BFC1-08002BE10318}, (default), "NetService"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E975-E325-11CE-BFC1-08002BE10318}, (default), "NetTrans"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E977-E325-11CE-BFC1-08002BE10318}, (default), "PCMCIA Adapters"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E97B-E325-11CE-BFC1-08002BE10318}, (default), "SCSIAdapters"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E97D-E325-11CE-BFC1-08002BE10318}, (default), "System"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E980-E325-11CE-BFC1-08002BE10318}, (default), "Floppy disk drive"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{71A27CDD-812A-11D0-BEC7-08002BE2092F}, (default), "Volume"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{745A17A0-74D3-11D0-B6FE-00A0C90F57DA}, (default), "Human Interfaces Devices"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\AFD, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\AppMgmt, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Base, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Boot Bus Extender, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Boot file system, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Browser, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\CryptSvc, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\DcomLaunch, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Dhcp, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dmadmin, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dmboot.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dmio.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dmload.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dmserver, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\DnsCache, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\EventLog, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\File system, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Filter, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\HelpSvc, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\ip6fw.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\ipnat.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\LanmanServer, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\LanmanWorkstation, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\LmHosts, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Messenger, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NDIS, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NDIS Wrapper, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Ndisuio, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetBIOS, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetBIOSGroup, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetBT, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetDDEGroup, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Netlogon, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetMan, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Network, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NetworkProvider, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\NtLmSsp, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\PCI Configuration, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\PlugPlay, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\PNP Filter, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\PNP_TDI, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Primary disk, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\rdpcdd.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\rdpdd.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\rdpwd.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\rdsessmgr, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\RpcSs, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\SCSI Class, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\sermouse.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\SharedAccess, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\sr.sys, (default), "FSFilter System Recovery"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\SRService, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Streams Drivers, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\System Bus Extender, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Tcpip, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\TDI, (default), "Driver Group"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\tdpipe.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\tdtcp.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\termservice, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\vga.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\vgasave.sys, (default), "Driver"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\WinMgmt, (default), "Service"
HKLM, SYSTEM\CurrentControlSet\Control\SafeBoot\Network\WZCSVC, (default), "Service"
[del]
HKCU, Software\Microsoft\Windows\CurrentVersion\RunMRU, a
HKCU, Software\Microsoft\Internet Explorer\Main, Window Title
HKLM, SOFTWARE\Microsoft\Windows\CurrentVersion\Run, Ageia
HKLM, SOFTWARE\Microsoft\Windows\CurrentVersion\Run, Systemdir
HKLM, SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system, EnableLUA
HKLM, SOFTWARE\Microsoft\Windows\CurrentVersion\Winlogon
Use notepad, then save with the name "repair.inf" (use the Save As Type option to be All Files to avoid an error occurred).
Repair.inf run with the right click, then select install.
· For cleaning the virus huhuhaha optimally and prevent re-infection, you should use anti-virus update and identify the virus with both.